Welcome to a world without privacy! If personal privacy is something you care about, now is the time to do something about it – before it’s too late. No one factor, but rather a confluence of movements has brought about the end of privacy. Underground surveillance capabilities of the U.S. government have ballooned since 9/11. Furthermore, they are similar to the spending and scope of secret Cold War infrastructure.
The transition from commerce to e-commerce, and the constant consumerism of the web have brought about massive changes. Increases in spending and innovation are substantial in data mining, tailored marketing, and online monitoring. For the unwary sharer online, even future employers or schools are potential transgressors on your “privacy.”
Today, whether private or public, benign or incendiary, every comment you make and every movement you take are subject to collection and analysis by someone. Welcome to the end of privacy.
Are Cell Phones Really Private?
No. You may not think your cell phone privacy matters unless you’re high profile person. However, the digital trail your cell phone leaves every day could end up haunting your Bourne Identity style someday. In an interview, Edward Snowden details what exactly can be done with your cell phone. “Any intelligence service in the world that has significant funding and a real technological research team can own that phone the minute it connects to their network,” Snowden notes.
“They can turn it into a microphone. They can take pictures with it. They can take the data off of it.”
Who Has a Right to Privacy?
The fourth amendment is meant to ensure people are secure in their persons, houses, papers, and effects against unreasonable searches and seizures. Without probable cause and a warrant, in theory, one should be safe from wiretaps and surveillance unless one has committed a crime and a warrant has been granted.
While this right has recently been extended in the 11th U.S. Circuit Court of Appeals in Atlanta, several other Federal appeals courts have reneged the right. Cell site location, as well as the abilities of the NSA to utilize cell phone hardware in the ways detailed by Snowden, have the capability to turn any otherwise private event into a public one.
Even in the event that you power off your phone, it has also been revealed that federal agencies can, in effect, force your phone to “play dead.” You may press the off button, receive the familiar buzz, and power off animations, while your phone can continue to record what’s going on, transmit location information, and so on. So what can you do?
The NSA and Co-Traveler
The NSA gathers 5 billion records a day on smartphone locations. Through a program known as “Co-Traveler” the NSA can discern who you are in the company of, and where you are based on cell tower coverage. Co-Traveler works by tracking the number of cell locations under a tower coverage area.
As cell locations change, the number of cells with the same unique travel path through tower coverage areas is winnowed down. After moving through several tower coverage areas, the chances that other cells have the same unique path through coverage areas is slimmer. With cell locations being tracked constantly, Co-Traveler can keep tabs on who you’re with, and where you go with relative ease.
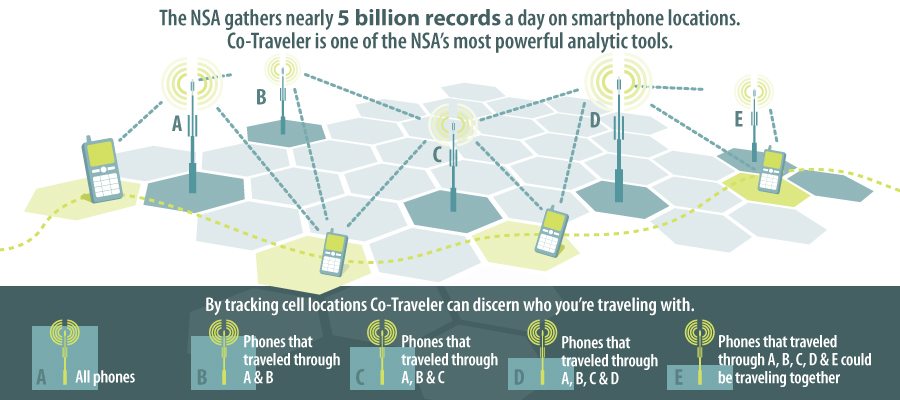
Short of simply leaving your cell phone at home, or switching between disposable cells often there aren’t many ways to escape the potential of being tracked by the Co-Traveler program. One ray of hope for your privacy, however, comes in the form of non-GPS-enabled phones.
GPS data can be tracked directly similar to the detail Google Maps can give you when providing directions. For older phones, or those without GPS tracking enabled, however, SIM card data must be used. This is often harder, and less exact, as it involves triangulating location based on calls to the cell tower.
Either way, capabilities are in place to track you through your cell. Moreover, the more modern the smartphone, the more ways in which it can be utilized for surveillance. Let’s just hope the NSA doesn’t have a reason to spy on most of us.
Facebook and Your Voluntary Privacy
While the same could be said for other social media platforms, Facebook’s popularity, privacy settings, and the way users use the platform make it a particularly insipid threat to privacy. We aren’t talking about the same type of privacy threat as the NSA with the ability to make a cell phone “play at sleep” while recording what’s going on. But rather a more gradual loss of privacy through what we voluntarily post online.
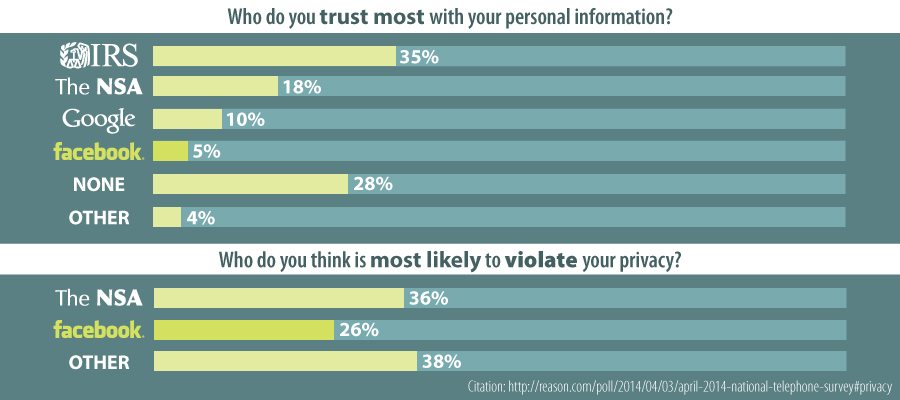
Who Do You Trust With Your Personal Information?
As of 2013, 13 million Facebook users had never touched their privacy settings. For many, this means that all of their posts, pictures, and interactions were available via public searches. Even for those who do monitor their privacy settings, the 2012 transition to the timeline dredged up old posts. This was a breath of new life into those pesky several-year-old photos you had hoped went away.
With periodic changes to the feed algorithm, it’s often hard to tell who might be seeing your activity without even asking to, or for whom your data is searchable. Messages are another potential privacy nightmare, and they’re currently stored indefinitely. Facebook’s changes are often made in the name of creating a better user experience. However, Facebook controls the flow of your information, and they may change it at their slightest whim.
Why is Privacy Important in Social Media?
But, you may already know all this about Facebook. You may even think it is simply the price you have to pay to be part of the modern, connected world. But, did you know these stats? Some 64% of employers check the Facebook and Twitter accounts of potential hires. More than 1/4 colleges screen applicants using social media. Social media posts are admissible in court, and even messages are admissible under traditional evidence rules. Coupled with location data and photos you create an indefinite record of whatever’s on your mind. So, you might want to think twice before sharing next time.
The disruption of a traditional level of privacy has led businesses to respond. Many want to limit your digital trail and pass laws to preserve your online privacy. Snapchat, the un-monetized sharing app was offered $2 billion for this service. Snapchat enables users to share messages and multimedia for a set number of seconds before it disappears. The price may seem ludicrous for an app that doesn’t currently make any money. However, it’s so high because they’re really on to what users want.
The EU has attempted to provide a remedy for information that’s already online, by preserving the “right to be forgotten” online when you die. While what this right means, in the end, is up for debate, the motive behind the ruling is clear. In a world of limitless data centers, you have a right for your digital footprint not to follow you forever.
Data Mining
The data mining industry highlights the true economic power of information. It gathers information on social media platforms, and search engines, and tracks user behavior on sites. It also shows the extent to which an internet-driven economy is a nightmare for personal privacy.
Don’t get us wrong, data mining is at the heart of online experiences tailored to the user. It’s also what helps the online industry create the products you like (House of Cards was made with data taken from Netflix users). If you just knew, however, how many personal details were stored in a data farm in Arkansas, you would probably be greatly freaked out.
How Does Data Mining Affect Privacy?
“Cookies,” or digital packets of information recording where you go, where you click, and how long you stay there online, are at the heart of data mining. True, you can’t log on to most sites without cookies, but they are a core component of gathering information on users. While a 2011 EU law requires consent from users for all cookies “non-essential” for the user’s use of the service.
The solution is highly impractical, both in enforcement, and in the motive to provide an ecosystem in which services online preserve users’ privacy, and can provide comparable services. In its original form, a strict rendering of the law would essentially disable the modern internet.
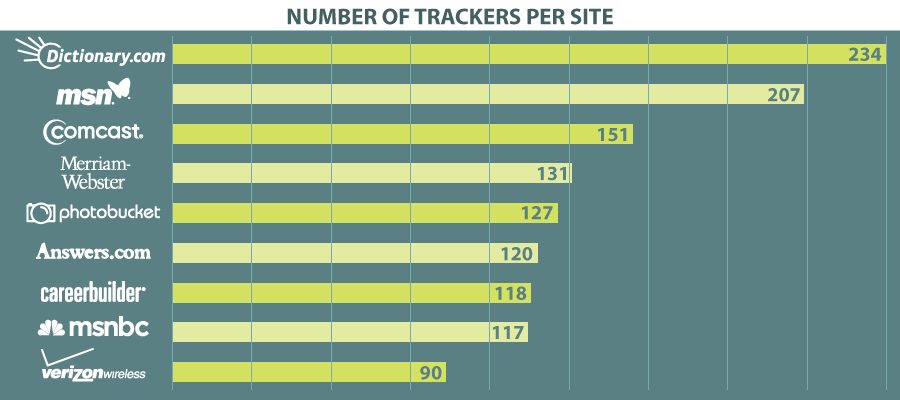
What are Some Pros and Cons of Data Mining?
A recent study of the 2,500 most popular sites online found that 87% had cookies. While there are certainly some cookies essential to keeping the sites working, a whopping 76% of cookies came from a total of 17,949 third-party hosts. With a total of 442,055 cookies in all (177 per site on average), you can bet your every click is recorded somewhere.
Data broker companies, or database marketers, perform the second component of data mining. The Acxiom Corporation is one such business, holding data points on over 500 million consumers worldwide and reviewing over 50 trillion data “transactions” yearly.
Based on data of individuals they track online, Acxiom places users into 70 “clusters” and 21 “life stages”. Then they use the information for marketing. Clusters and life stages descriptions are with pithy phrases, and if you would like to check out what Acxiom thinks of you, you can check out your profile here.
Why is Data Privacy Important?
It’s yet to be seen if preserving what little privacy we have left involves reining in the surveillance capabilities of both public and private entities. Or, if the loss of privacy is just the cost we must pay for living in a connected world. What is clear is that, if personal privacy is something you care about, now is the time to do something about it. Before it’s too late.
So, if personal privacy is something you care about, now is the time to do something about it.
Related:
- 10 Best Android Security Apps
- Apps and Privacy
- 10 Best iPhone Security Apps
- Best Free Cybersecurity Courses Online